In this article, we examine how supply chain disruptions in minerals, electronics, and skilled labor are creating risks and opportunities in the US Defense Industrial Base (USDIB).
Minerals: Rare Earth Elements
The USDIB relies on Rare Earth Elements (REEs). REEs, loosely defined, are a set of 17 nearly indistinguishable lustrous silvery-white soft heavy metals. The term 'rare-earth' is misleading because they are not actually scarce. REEs are common throughout the Earth's crust. However, because of their geochemical properties, most REEs are highly dispersed as trace elements. Geological regions with relatively high concentrations of REE are rare and even in these rare instances, obtaining usable quantities of pure REEs requires processing enormous amounts of raw material at great expense.
REE is mined by first removing rock from the ground that contains the REE. Most rare-earth ores are mined by conventional open-pit methods in which rock is broken by blasting, loaded onto trucks with large shovels, and hauled to a concentration facility. Concentration is by physical separation of the REE-bearing minerals from all other minerals in the rock. The ore is crushed and ground in multiple stages until most of the rare-earth minerals interlocked with the other minerals are broken free. Next, in a method known as froth flotation, the rare-earth minerals are coated with a chemical that repels water and allows them to float to the surface attached to air bubbles in agitated tanks, where they are skimmed off as a concentrate. The remaining minerals are disposed of as waste and the REE concentrate is then ready for leaching.
The REE concentrate is then leached with an acid and the resulting REE-rich solution is then processed through sequential steps to recover individual REEs. For example, Cerium can be recovered by the addition of sodium hydroxide, which causes the cerium to drop out of solution as an oxide or hydroxide. The other REEs are typically separated by solvent extraction, a process in which an organic chemical specially designed to extract a particular REE is forced countercurrent to the REE-bearing leach solution. Mining and concentration of REE ores presents conventional problems of concentrate waste disposal. For every ton of REEs produced, the process yields an estimated 75 cubic meters of wastewater and one ton of radioactive residue.

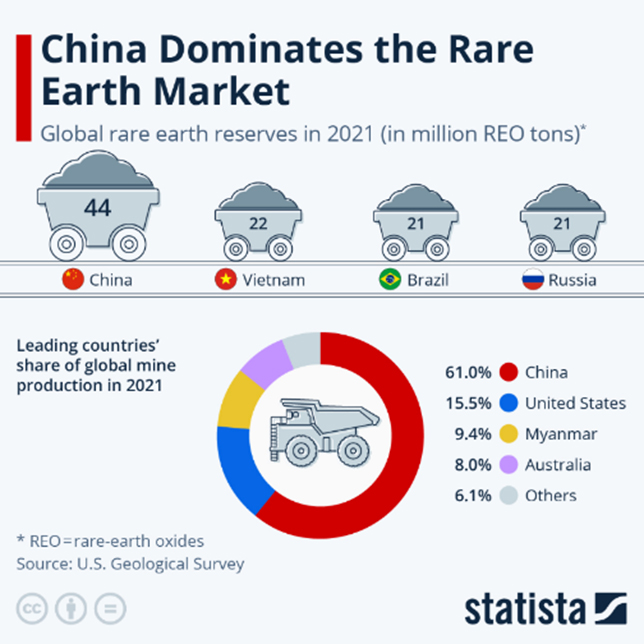
From the mid-1960s to the early 1990s, the United States was the world’s largest REE-producing country, with production coming entirely from the Mountain Pass mine in southeastern California. The mine was discovered in 1949 by a uranium prospector. The mine is located in San Bernardino County, California, on the south flank of the Clark Mountain Range. The mine has been active since 1952, with production expanding in the 1960s. In 2020, the mine supplied 15.8% of the world's rare-earth production. Today the mine is owned by MP Materials Corp (NYSE: MP). At this time, MP Materials Corp. is the largest producer of rare earth materials in the Western Hemisphere. The company recently raised $1B to expand its capacity. The Mountain Pass mine is currently the only active REE mine in the United States.
In the late 1980s, China began mining their in-country REE deposits, processing their ore and extracting and separating the individual REEs for use in products, which they also manufactured. China quickly gained control of global REE production, providing 95 percent of the global market of processed REE by 2011. Between 2011 and 2017, China produced approximately 84 percent of the world’s REEs.

China was able to establish dominance over the REE industry in large part because of its lower environmental regulations. Low cost, high pollution extraction methods enabled China to outpace competitors and create a strong foothold in the international REE market. The largest REE mine in the world at this time is the Bayan-Obo mine in China. At this mine, there are an estimated 70,000 tons of radioactive thorium waste in storage ponds in the area. These waste ponds are not far from the Yellow River and there is concern that they could eventually leach into the river, which is a key source of drinking water for a substantial population. To maintain its dominance in REEs, China is also in the process of expanding its REE mining operations outside of mainland China. China has obtained rights to the REE deposits in a handful of African countries in return for infrastructure investment, including but not limited to the Democratic Republic of the Congo in return for building national roads, highways, and hospitals. China has obtained commercial licenses for REE mines in Kenya by agreeing to build a $600+ million data center.
President Trump’s recent comments that he wants the US to “purchase Greenland” have made international headlines. While we will not comment on the politics of this, we are glad to comment on one of the reasons why he said this. One reason was the Kvanefjeld deposit in Greenland is estimated by scientists to be one of the largest known REE deposits on earth. China has been in discussions with Greenland since 2017 about gaining rights to mine Kvanefjeld. To date, Greenland has rejected China’s offers regarding Kvanefjeld. Given that much of the Island has not yet been fully explored for REEs, many scientists believe that Greenland may hold substantial REE deposits. Furthermore, with receding Artic Ice (due to global warming), the costs of extracting REEs from Greenland are expected to decline significantly.
Electronics: Computer Chips
Semiconductors and advanced electronics form the technological backbone of modern defense systems, powering communications, surveillance, and weapons guidance. However, the semiconductor industry has been plagued by significant supply disruptions. A global chip shortage that began with the COVID – 19 pandemic in 2020 has persisted, driven by surging demand, throughput constraints, and an overreliance on semiconductor fabs in Taiwan. Furthermore, China has made the leadership in the semiconductor industry a national strategic objective. According to the US based Semiconductor Industry Association, China has plans to invest more than $150 Billion in the sector between 2014 and 2030.
The U.S. government responded in 2022 with the Creating Helpful Incentives to Produce Semiconductors Act (CHIPS), which authorized $280 Billion to boost domestic research and manufacturing in the semiconductor industry in the US. In addition to this substantial amount of funding, the CHIPS Act also authorized Department of Commerce (DOC), Department of Defense (DoD), and Department of State (DOS) the authority to waive certain regulations to expedite the development of onshore domestic manufacturing of semiconductors critical to U.S. competitiveness and national security. The Act also includes safeguards to ensure that companies that receive Federal funds from the Act cannot use those funds to build advanced semiconductor production facilities in countries that present a national security threat to the US. When announcing the Act, congress noted that only 12% of chips are currently manufactured domestically, compared to 37% in the 1990s.
Other specific provisions of the Act included:
• $39 billion in immediate financial assistance to build, expand, or modernize domestic facilities and equipment for semiconductor fabrication
• $11 billion for DOC research and development.
• $2 billion for the DoD to implement the Microelectronics Commons, a national network for onshore, university-based prototyping, lab-to-fab transition of semiconductor technologies
• Waivers of certain environmental and other regulatory requirements necessary to construct and operate new semiconductor fabrication facilities
Skilled Labor
While supplies of REEs and advanced semiconductors are crucial to the USDIB, a skilled workforce in manufacturing remains the most essential component of the defense supply chain. The USDIB is experiencing a severe shortage of qualified manufacturing professionals, from engineers to machinists. Several factors contribute to this challenge, including an aging workforce and insufficient training pipelines for specialized defense roles. This talent gap not only hampers production schedules but also slows innovation.
Today, the manufacturing sector is not a top choice for the newest generation of workers. Just 14% of Gen Zers say they would consider a career in manufacturing, because of expectations of: low pay and dangerous work conditions. Their disinterest has resulted in a rapidly aging workforce. About 51% of manufacturing jobs are held by employees ages 45-65 or older (Clear Company, manufacturing-workforce-trends-development-strategies, 2025).
There are some near-term solutions to this problem. Employers can establish apprenticeship programs in collaboration with local technical schools to build a pipeline of future talent. These programs are increasingly recognized as critical for addressing the workforce shortages in defense manufacturing. The Department of Defense's Manufacturing Education and Workforce Development (M-EWD) Program, for instance, collaborates with industry stakeholders to create skilled professionals who are equipped to meet the demands of advanced manufacturing. This initiative focuses on bridging the gap between educational systems and real-world manufacturing needs. Also, ensuring that workers are prepared for the technology-driven advancements in defense sectors such as artificial intelligence, robotics, and advanced materials. This proactive approach not only helps close the skills gap but also strengthens the pipeline of human capital for middle market defense companies by providing students with valuable, career-oriented training in high-demand fields. Employers can partner with higher education institutions to create specialized training initiatives tailored to defense sector needs. Such partnerships are essential for ensuring that the talent entering the defense industry has the precise skills required for the evolving technological landscape. The Aerospace Industries Association (AIA) plays a leading role in advocating for the development of specialized training, reskilling, and educational programs that align with the needs of the defense industry. By working with colleges and universities, defense companies can ensure that curricula are closely aligned with current and future technological demands, such as cybersecurity, artificial intelligence, and aerospace engineering. These initiatives also help cultivate a more adaptable workforce, equipped to handle the rapid pace of innovation in the sector.
Weapons Manufacturing Capacity
In 2024, the Center for Strategic & International Studies (CSIS) reported that China’s defense industrial base is operating on a wartime footing, while the U.S. defense industrial base is largely operating on a peacetime footing. The report went on to state that “the U.S. defense industrial ecosystem lacks the capacity, responsiveness, flexibility, and surge capability to meet the U.S. military’s production and warfighting needs.” Unless there are urgent changes, the United States risks weakening deterrence and undermining its warfighting capabilities. China is heavily investing in munitions and acquiring high-end weapons systems and equipment five to six times faster than the United States. China is also the world’s largest shipbuilder and has a shipbuilding capacity that is roughly 200 times larger than the United States. According to the CSIS 2024 report, China’s largest shipyard, Jiangnan, has more capacity than all U.S. shipyards combined.
While the pandemic was not the only cause of this problem, it was certainly a catalyst. Lockdowns and business closures set off supply chain disruptions that led to a 43% decline in all US manufacturing output and a 38% drop in hours worked, the largest since World War II, and manufacturers were forced to lay off their employees. Some of the 1.4 million workers across all sectors, who lost their jobs left permanently, whether they retired early, began working in a different industry, or left the workforce for other reasons.
In the years since, US manufacturing has had an impressive recovery. The industry has added nearly 800,000 jobs since 2021. According to the National Association of Manufacturers (NAM) Manufacturers’ Outlook Survey, companies’ optimism about their future is rising. Even with growth, manufacturing still anticipates a long struggle with the talent shortage. Despite the addition of so many jobs, almost 550,000 are currently vacant, and research from Deloitte and The Manufacturing Institute indicates that this number will increase. An estimated four million manufacturing employees will be needed by 2030 in the US.
What This Means for Middle-Market Defense Contractors
From our vantage point as M&A bankers in the middle market of the aerospace & defense industry, we have a unique view. We can see what is happening in real-time in the supply chain. We hear from the owners of these companies - what keeps them up at night. And we hear from the buyers of these companies - what opportunities they see and why they are making substantial investments.
The Risks
There are three risks facing the middle market of the USDIB that we keep hearing:
• First, China is the biggest single threat to the US, not just terms of the risk of kinetic attack, but moreover in terms of non-kinetic warfare, including but not limited to the disruption of critical supply chains.
• Second, behind ‘China Risk’, is the risk of an aging USDIB manufacturing workforce
• Third, is the lack of investment into USDIB manufacturing infrastructure for decades
The Opportunity
While the risks facing the USDIB are substantial, the opportunity facing the middle market of the USDIB is even greater. Today, we are hearing repeatedly and loudly, especially from active buyers in the sector, the following:
• Manufacturing throughout the USDIB will experience a significant resurgence over the next 3-5 years, in terms of demand from the Department of Defense, the influx of new workers, and the flow of investment capital.
By Bruce Andrews, Partner and Troy Medeiros, Vice President, Alderman And Company