DHS Issues National Terrorism Advisory System (NTAS) Bulletin

The Secretary of Homeland Security Alejandro N. Mayorkas has issued a National Terrorism Advisory System (NTAS) Bulletin regarding the continued heightened threat environment across the United States. This is the fifth NTAS Bulletin issued by the Department of Homeland Security since January 2021.
“DHS remains committed to proactively sharing timely information and intelligence about the evolving threat environment with the American public,” said Secretary Alejandro N. Mayorkas. “We also remain committed to working with our partners across every level of government and in the private sector to prevent all forms of terrorism and targeted violence, and to support law enforcement efforts to keep our communities safe. This NTAS Bulletin outlines the key factors that have increased the volatility, unpredictability, and complexity of the current threat environment, and highlights resources for individuals and communities to stay safe.”
The United States remains in a heightened threat environment fueled by several factors, including an online environment filled with false or misleading narratives and conspiracy theories, and other forms of mis- dis- and mal-information (MDM) introduced and/or amplified by foreign and domestic threat actors. These threat actors seek to exacerbate societal friction to sow discord and undermine public trust in government institutions to encourage unrest, which could potentially inspire acts of violence. Mass casualty attacks and other acts of targeted violence conducted by lone offenders and small groups acting in furtherance of ideological beliefs and/or personal grievances pose an ongoing threat to the nation.
While the conditions underlying the heightened threat landscape have not significantly changed over the last year, the convergence of the following factors has increased the volatility, unpredictability, and complexity of the threat environment: (1) the proliferation of false or misleading narratives, which sow discord or undermine public trust in U.S. government institutions; (2) continued calls for violence directed at U.S. critical infrastructure; soft targets and mass gatherings; faith-based institutions, such as churches, synagogues, and mosques; institutions of higher education; racial and religious minorities; government facilities and personnel, including law enforcement and the military; the media; and perceived ideological opponents; and (3) calls by foreign terrorist organizations for attacks on the United States based on recent events.
DHS and the Federal Bureau of Investigation (FBI) continue to share timely and actionable information and intelligence with the broadest audience possible. This includes sharing information and intelligence with our partners across every level of government and in the private sector. Under the Biden-Harris Administration, DHS is prioritizing combating all forms of terrorism and targeted violence, including through its efforts to support the first-ever National Strategy for Countering Domestic Terrorism. Since January 2021, DHS has taken several steps in this regard, including:
- established a new domestic terrorism branch within DHS’s Office of Intelligence and Analysis dedicated to producing sound, timely intelligence needed to counter domestic terrorism-related threats;
- launched the Center for Prevention Programs and Partnerships (CP3) to provide communities with resources and tools to help prevent individuals from radicalizing to violence;
- designated domestic violent extremism as a “National Priority Area” within DHS’s Homeland Security Grant Program for the first time, resulting in at least $77 million being spent on preventing, preparing for, protecting against, and responding to related threats nationwide;
- provided $180 million in funding to support target hardening and other physical security enhancements to non-profit organizations at high risk of terrorist attack through DHS’s Nonprofit Security Grant Program (NSGP);
- increased efforts to identify and evaluate MDM, including false or misleading narratives and conspiracy theories spread on social media and other online platforms, that endorse violence; and,
- enhanced collaboration with public and private sector partners – including U.S. critical infrastructure owners and operators – to better protect our cyber and physical infrastructure and increase the Nation’s cybersecurity through the Department’s Cybersecurity and Infrastructure Security Agency (CISA).
DHS also has renewed its commitment to ensure that all efforts to combat domestic violent extremism are conducted in ways consistent with privacy protections, civil rights and civil liberties, and all applicable laws.
This NTAS Bulletin will expire on June 7, 2022. This NTAS Bulletin provides the public with information about the threat landscape facing the United States, how to stay safe, and resources and tools to help prevent an individual’s radicalization to violence. The public should report any suspicious activity or threats of violence to local law enforcement, FBI Field Offices, or a local Fusion Center.




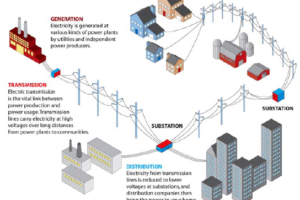
 A stable homeland is dependent on the reliable delivery of electricity—from public health to the economy and national security. According to DOE's Grid Modernization and the Smart Grid project, there are more than 9,200 electric generating units with more than 1 million megawatts of generating capacity feeding more than 600,000 miles of transmission lines that comprise the U.S. electric grid.
A stable homeland is dependent on the reliable delivery of electricity—from public health to the economy and national security. According to DOE's Grid Modernization and the Smart Grid project, there are more than 9,200 electric generating units with more than 1 million megawatts of generating capacity feeding more than 600,000 miles of transmission lines that comprise the U.S. electric grid.



